What is Ransomware?
What You Need to Know About the Malware that Hits Your Data, and Then Your Wallet
Cybercriminals have no shortage of tools at their disposal in their attempts to abuse and take advantage of those they set their sights on. Recently, however, it seems that more and more of them select ransomware as their weapon of choice. Knowing what ransomware is, and how to avoid falling victim to it, is critical to a business’ survival. Fortunately, this particular malware has a few distinct characteristics that make it relatively simple to identify and describe.
Why does it seem like ransomware is popular among online actors with ill intent?
Like many online attacks, ransomware is very descriptively summed up by its name–simply put, it’s malware that allows hackers to demand a ransom. This malware classification follows a simple, but devious, method of attack: the program will encrypt files on the host system and demand that the user pay to regain access to their files, typically asking to be paid in some form of cryptocurrency. To add a sense of urgency to this demand, the extortionist will include a time limit within their demands, threatening to either delete the files or double the amount demanded if the stated deadline passes.
Due to the typically high ransoms that are associated with ransomware, there are some targets that tend to be assaulted more than others. After all, a cybercriminal’s motivation for utilizing ransomware is financial, and so they will be more apt to attack targets with more capital and higher liquidity. This means that businesses are much more likely to be targeted than a private user, although the latter is not unheard of.
How is ransomware spread?
A favorite tactic of malware distributors is the use of email phishing, or sending out deceptive emails that look to fool the recipient into allowing the malware to access their system. These emails can appear to be from a variety of senders, from government organizations to industry peers, and can often be very convincing. The malware is sent along as an attachment that executes once it is opened, bypassing many of the system’s defenses through the user’s permission.
This tendency for malware to spread via phishing provides two more reasons that businesses are so frequently designated as targets: camouflage and points of access.
Business users tend to get lots of emails. Clients, coworkers, and the assorted other contacts that reach the inbox as an employee does their work will give an employee plenty to review, which eventually will lead to the employee managing their email on autopilot. After a member of Human Resources has been working for a while, a folder containing job application materials may not be an out-of-the-ordinary thing for them to receive. If the corrupted email looks legitimate, what cause would an employee have to worry? These assumptions (the ones that lead to short-sighted clicking) are precisely what cybercriminals rely on to infiltrate their victims’ systems.
The other contributing factor to a business is related to these assumptions as well: a high volume of points of access. As they grow, businesses will usually need to take on more employees to support their operations. An unfortunate side effect of this, however, is that as a company grows in potential value to a cybercriminal, it also increases the number of potential access points for a cybercriminal to take advantage of.
Ransomware Titles You Should Know
CryptoLocker
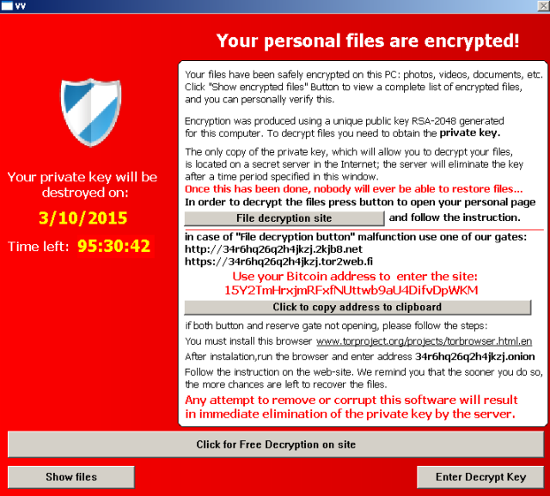
Zepto
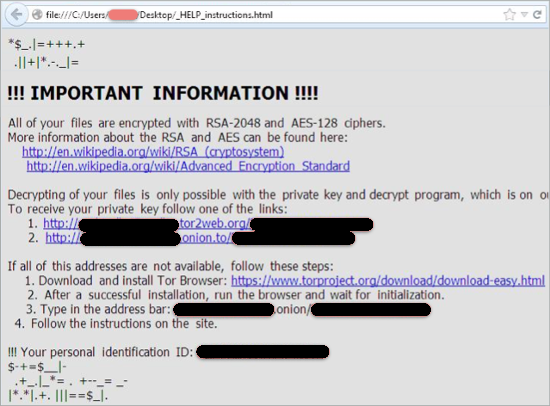
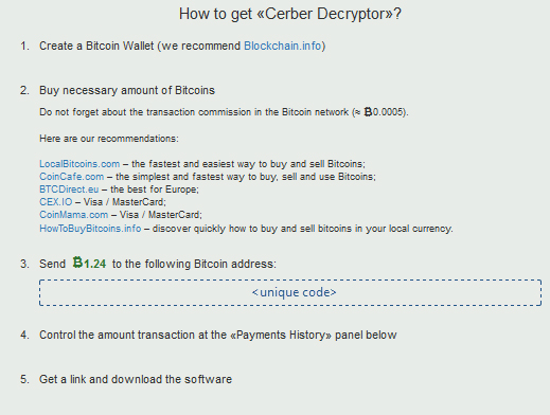
Cerber3
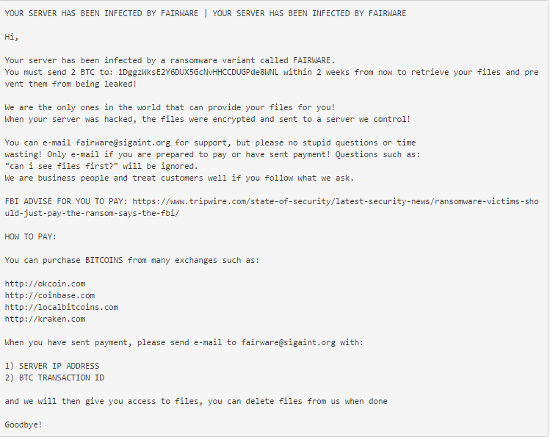
FairWare
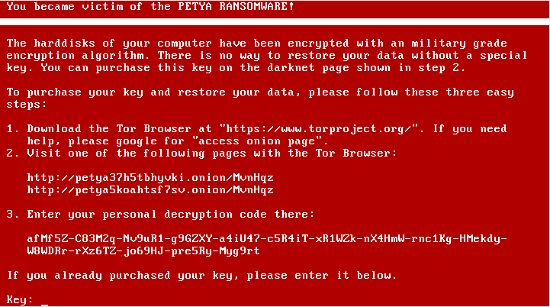
Petya
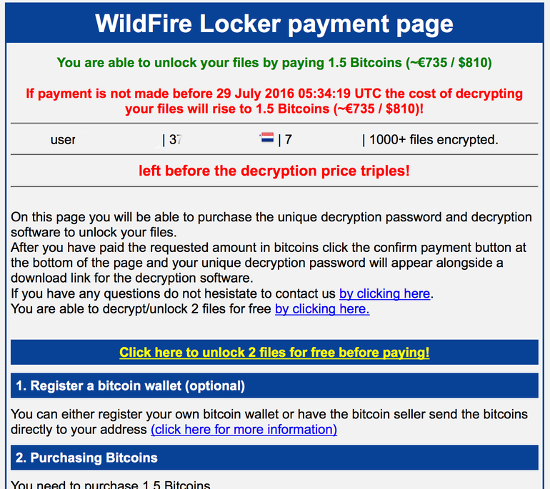
Wildfire